Compensation data represents one of the most sensitive information assets within organizations, requiring robust privacy practices, secure access controls, and comprehensive management protocols. As pay transparency requirements expand and employee expectations for data security intensify, HR departments must implement sophisticated data privacy frameworks that balance transparency obligations with confidentiality requirements. This white paper outlines best practices for compensation data privacy and provides actionable guidance for implementing standard operating procedures that protect sensitive information while supporting strategic talent management objectives.
Foundation of Compensation Data Privacy Best Practices
Risk Assessment and Compliance Framework
Compensation data privacy starts with a detailed risk assessment that identifies vulnerabilities, aligns practices with GDPR and state privacy laws, and evaluates organizational exposure to data breaches. HR teams must evaluate current practices against legal standards including GDPR, state privacy laws, and industry-specific regulations while considering reputational risks associated with data breaches.*
Critical Risk Considerations:
- Unauthorized access to individual salary information and compensation decisions
- Data breach exposure resulting in competitive intelligence loss and employee privacy violations
- Regulatory non-compliance with federal and state privacy requirements
- Internal misuse of compensation data for discriminatory or inappropriate purposes
- Third-party vendor access and data sharing vulnerabilities
Organizations experiencing compensation data breaches face average costs of $4.4 million including legal fees, regulatory penalties, and reputational damage, making preventive privacy practices essential investments.*
Data Classification and Sensitivity Levels
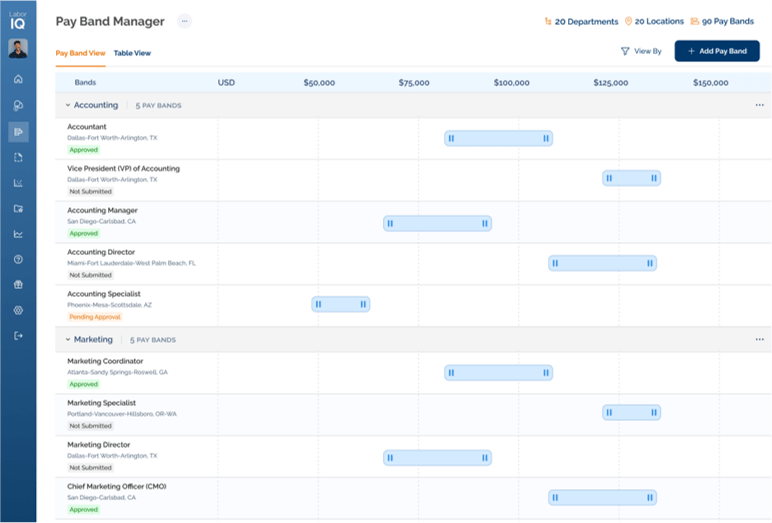
Establishing a clear data classification system helps HR leaders apply the right security controls for each level of compensation data sensitivity, strengthening overall data governance. Compensation data should be categorized by confidentiality requirements, enabling tiered access protocols and proportionate security measures.*
Classification Framework:
- Highly Confidential: Individual employee salary data, executive compensation, equity grants
- Confidential: Department budgets, aggregate compensation analysis, market benchmarking data
- Internal Use: Pay band structures, compensation philosophy documents, general policies
- Public Information: Salary range disclosures required by transparency laws, publicly filed executive compensation
Standard Operating Procedures for Access and Management
Role-Based Access Controls (RBAC)
Implementing role-based access controls ensures only authorized personnel access compensation data based on legitimate business needs. This principle of least privilege minimizes exposure while enabling necessary operational functions.*
Access Level Framework:
- Executive Leadership: Complete access to organizational compensation data and strategic analysis
- HR Leadership: Comprehensive access for policy development, analysis, and compliance management
- HR Generalists: Limited access to specific employee data within assigned departments or regions
- Managers: Access only to direct report compensation information with time-limited permissions
- Employees: Self-service access to personal compensation information and applicable policies
Organizations implementing RBAC report 70% reduction in unauthorized access incidents and 85% improvement in audit compliance.*
Data Access Documentation and Audit Trails
Comprehensive logging and monitoring of all compensation data access enables detection of unauthorized activities, supports compliance audits, and ensures accountability throughout the organization.*
Essential Documentation Requirements:
- User authentication and authorization records for all system access
- Detailed audit trails tracking data queries, modifications, and exports
- Regular access reviews validating continued business need for permissions
- Incident response logs documenting security events and remediation actions
- Annual compliance certifications confirming adherence to privacy protocols
Secure Data Storage and Transmission Protocols
Protecting compensation data requires encryption, secure storage systems, and controlled transmission methods that prevent unauthorized interception or access.*
Technical Security Measures:
- End-to-end encryption for data in transit and at rest
- Multi-factor authentication for all compensation system access
- Secure file transfer protocols for external data sharing
- Regular security assessments and penetration testing
- Automated backup and disaster recovery procedures
Balancing Privacy with Pay Transparency Requirements
Structured Transparency Frameworks
Modern privacy practices must accommodate increasing pay transparency obligations while protecting individual employee information and maintaining competitive positioning.*
Privacy-Preserving Transparency Approaches:
- Salary range disclosures without individual employee identification
- Aggregate compensation analysis by job family or department
- De-identified pay equity reporting protecting individual privacy
- Clear communication distinguishing public transparency from internal confidentiality
- Structured processes for handling employee compensation inquiries within privacy guidelines
Organizations that balance data privacy with pay transparency build stronger employee trust and demonstrate higher compliance with data protection standards.*
Third-Party Vendor Management
Compensation management often involves external vendors requiring access to sensitive data. Robust vendor management protocols ensure third parties maintain equivalent privacy standards.* Leveraging compensation data platforms like LaborIQ which provide detailed permissions access levels for company leaders, helps create structure and uphold privacy policies.
Vendor Due Diligence Requirements:
- Comprehensive security assessments before data sharing authorization
- Contractual obligations specifying data protection requirements and liability
- Regular audits validating vendor compliance with privacy commitments
- Limited data sharing based on strict need-to-know principles
- Incident response protocols for vendor-related security events
HR’s Strategic Role in Privacy and Compensation Management
Policy Development and Governance
HR departments lead development of comprehensive privacy policies, governance frameworks, and operational procedures ensuring consistent application across the organization.*
Policy Framework Components:
- Clear data handling procedures for all compensation-related activities
- Privacy training requirements for all employees with data access
- Incident response protocols addressing potential breaches or violations
- Regular policy reviews updating requirements based on regulatory changes
- Cross-functional governance committees overseeing privacy program effectiveness
Training and Culture Building
Effective privacy practices require organizational culture supporting data protection as fundamental value rather than compliance obligation.*
Training Program Elements:
- Mandatory privacy training for all HR personnel handling compensation data
- Manager education on confidentiality obligations and appropriate data discussions
- Employee communication regarding privacy rights and data protection measures
- Regular refresher training addressing emerging threats and updated requirements
- Consequences for privacy violations clearly communicated and consistently enforced
Organizations investing in comprehensive privacy training experience 60% fewer security incidents and 75% faster incident detection and response.*
Continuous Improvement and Adaptation
Compensation data privacy requires ongoing evaluation, updating, and enhancement as threats evolve and business requirements change.*
Continuous Improvement Processes:
- Regular privacy assessments identifying vulnerabilities and improvement opportunities
- Monitoring of emerging privacy regulations and best practice developments
- Technology updates ensuring systems maintain current security standards
- Feedback mechanisms capturing employee concerns and improvement suggestions
- Annual comprehensive privacy program reviews validating effectiveness
Measuring Privacy Program Success
Key Performance Indicators:
- Zero unauthorized access incidents and data breaches
- 100% completion rates for mandatory privacy training programs
- Audit compliance scores exceeding 95% across all privacy requirements
- Employee confidence scores related to compensation data protection
- Incident response time averaging under 2 hours for security events
Conclusion
Compensation data privacy represents a critical organizational responsibility requiring systematic approaches, robust technical controls, and sustained management commitment. HR departments that implement comprehensive privacy practices protect sensitive employee information while supporting transparency obligations and strategic talent management objectives. The investment in privacy infrastructure, training, and governance delivers measurable value through risk mitigation, regulatory compliance, and enhanced employee trust. Organizations prioritizing compensation data privacy position themselves for sustainable success in environments demanding both transparency and confidentiality.
Sources:
- Society for Human Resource Management (SHRM): https://www.shrm.org
- International Association for Privacy Professionals (IAPP): https://iapp.org
- National Institute of Standards and Technology (NIST) Privacy Framework
- State privacy law resources and regulatory guidance
- Cybersecurity and Infrastructure Security Agency (CISA): https://www.cisa.gov
- Employment law firms specializing in data privacy and compensation practices